Valyn
Secure your AI. Protect your data.

What is Valyn?
As enterprises adopt AI, one major challenge remains: keeping sensitive data safe. The AI Data Protection App acts as a smart middleware layer between internal systems and AI models, automatically redacting personally identifiable information (PII) and sensitive fields before they reach or leave the model. It ensures every AI interaction meets enterprise-grade security and compliance standards without slowing down innovation.
Beyond redaction, the system detects prompt-injection attempts and other data-exfiltration risks in real time, protecting intellectual property and customer trust. Designed for compliance-focused industries such as finance, healthcare, and government, it helps teams deploy AI confidently while maintaining full auditability and control.
Real-time Data Pseudonymization
Instantly remove PII and sensitive details from prompts and responses in real-time.
Prompt Injection Defense
Detect and block malicious prompt manipulations before they cause leaks.
Primary Use Cases
Valyn addresses critical security challenges in enterprise AI deployments across sensitive industries. Each use case demonstrates how our security middleware prevents costly compliance breaches and data exposure incidents.
PII Redaction in Outbound Queries to Model Server Endpoints
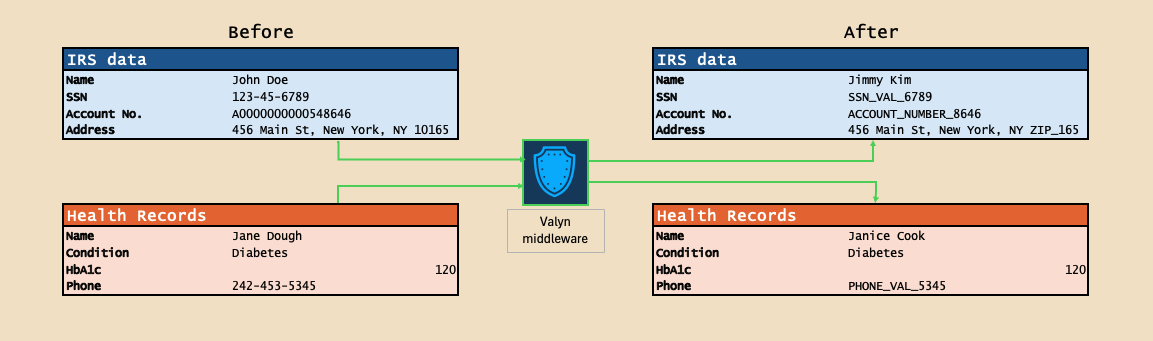
- Valyn Enterprise licensing ($80k-120k annually) ≪ Legal costs (millions) - A single data breach can result in millions in legal fees, regulatory fines, and reputation damage
- Automatic detection and redaction of PII, PHI, and sensitive data before queries reach external AI models
- Real-time compliance validation for HIPAA, GDPR, CCPA, and SOX requirements
- Seamless integration with OpenAI, Anthropic, and other cloud-based AI providers
The most powerful AI models today—GPT-4, Claude, Gemini—remain hosted on cloud infrastructure by major AI companies. Healthcare organizations, legal firms, and financial institutions need to leverage these cutting-edge capabilities while maintaining strict compliance with privacy regulations. Any customer data leakage to these external systems can trigger massive legal liability, regulatory investigations, and loss of professional licenses.
Valyn acts as an intelligent proxy layer, automatically identifying and redacting sensitive information before it leaves your network perimeter. This enables organizations to harness the full power of state-of-the-art AI models while ensuring zero exposure of protected data. The system maintains detailed audit logs of all redactions and data flows, providing the documentation necessary for compliance audits and regulatory reporting.
LLM Prompt Injection Defense for On-Premises Agents
Supported Security Models:
Choose the model that best fits your security requirements and infrastructure constraints.
- Advanced detection of malicious prompt injection attempts targeting internal AI agents
- Multiple security models (Llama Guard, Granite Guardian, ShieldGemma) provide continuous screening and keyword-based blocking
- Real-time prevention of unauthorized access to internal tools and databases
- Configurable security policies for different agent roles and access levels
On-premises AI agents with access to internal tools, databases, and systems represent a significant security risk if not properly hardened. These agents often have elevated privileges to perform complex tasks across enterprise infrastructure. A successful prompt injection attack could lead to unauthorized data access, system manipulation, or complete data exfiltration—creating non-recoverable data loss and massive financial liability.
Valyn integrates industry-leading security models including Meta's Llama Guard, IBM's Granite Guardian, and Google's ShieldGemma to provide continuous, real-time screening of all prompts sent to on-premises agents. The system employs sophisticated pattern recognition to identify injection attempts, malicious keywords, and suspicious command sequences. When threats are detected, Valyn immediately blocks the request and logs the incident for security team review. This multi-layered defense ensures that even if user inputs contain malicious instructions, they never reach your critical AI agents or internal systems.
Robotics Boundary Enforcement
- Coordinate-based access control for embodied AI systems and autonomous robots
- Real-time X,Y coordinate validation against predefined boundary rules
- Dynamic zone management for different robot roles and functions
- Emergency override capabilities for authorized personnel
As embodied AI systems and autonomous robots become more prevalent in enterprise environments, physical access control becomes critical. Consider a laundry service robot in a hotel—it should have full access to guest rooms and laundry facilities but must be prevented from entering the kitchen, server room, or management offices. Traditional security measures often rely on physical barriers, but AI-driven robots require more sophisticated digital boundary enforcement.
Valyn's middleware continuously monitors robot location requests and validates them against pre-configured spatial boundaries. When a laundry robot attempts to access kitchen coordinates (X: 150-200, Y: 75-100), the system immediately blocks the request and can trigger alternative routing or return-to-base commands. This ensures that even if a robot's navigation system is compromised or receives incorrect instructions, it cannot physically access restricted areas. The system maintains detailed logs of all movement requests and boundary violations for security analysis and compliance reporting.
Security Through Isolation
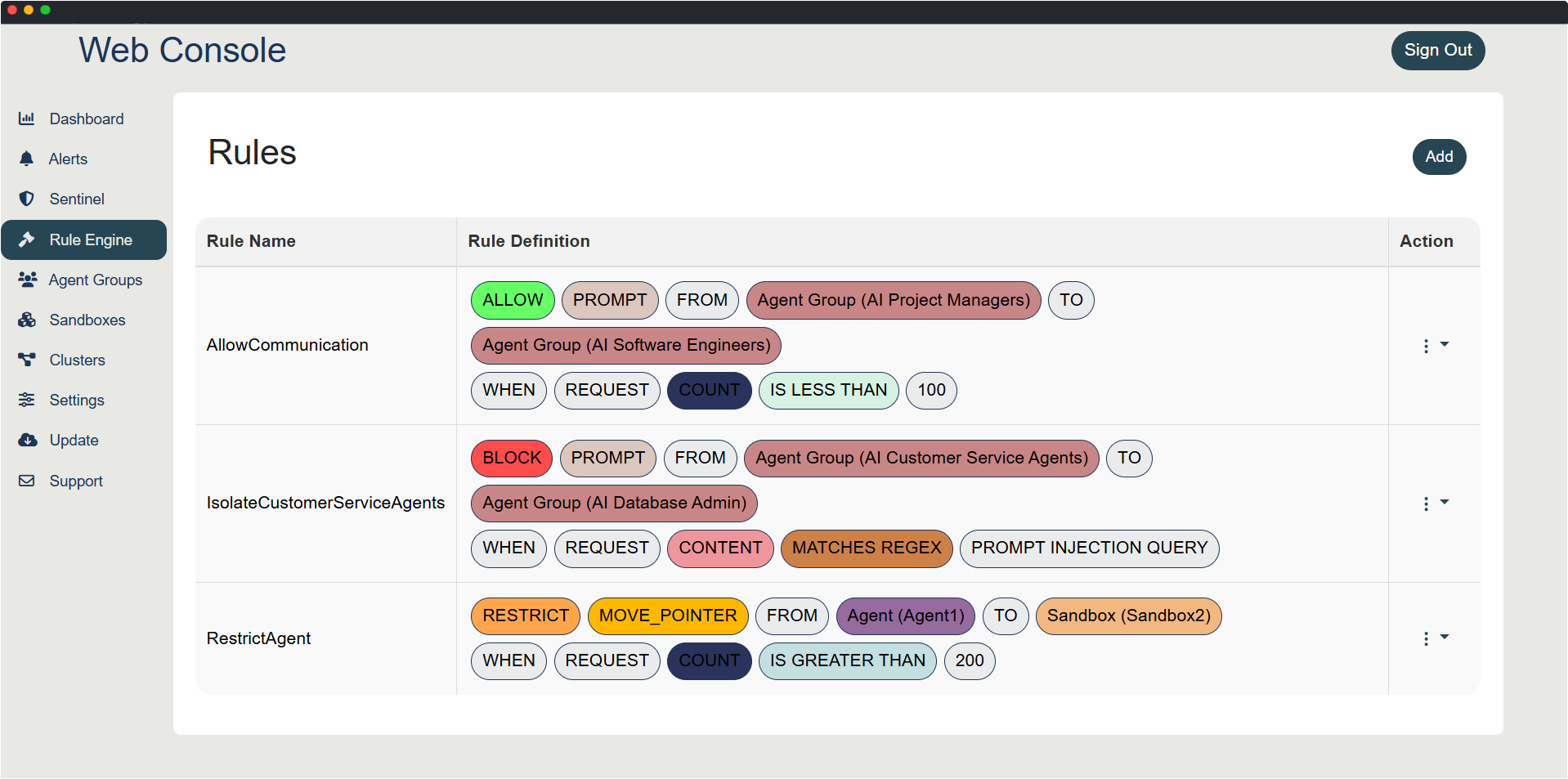
- Network-level isolation between Access Nodes (data collection) and Agent Nodes (processing)
- Advanced firewall rules preventing unauthorized internet access from Agent Nodes
- Active inter-agent communication monitoring and threat detection
- Behavioral analysis to identify compromised agents attempting lateral movement
In a multi-agent enterprise deployment, proper network isolation is crucial for preventing attack propagation. Access Nodes collect and pre-process data from various sources, while Agent Nodes run the actual AI processing workloads. These components must be isolated to prevent a compromise in one system from affecting others. A sophisticated firewall architecture ensures that Agent Nodes cannot initiate unauthorized internet connections, preventing data exfiltration and malware downloads.
Attack Scenario Example: A customer service agent becomes compromised through prompt injection or misconfiguration and attempts to download ransomware from the internet. In a properly isolated deployment, this request is blocked by firewall rules. The compromised agent then tries to convince a tool-calling agent to download and execute the malicious payload. However, Valyn's active inter-agent monitoring platform detects this unusual communication pattern, recognizes the potential threat, and immediately blocks the request while alerting security teams. This multi-layered defense prevents the attack from succeeding and contains the compromise to a single agent node.
Key Features
Real-time Monitoring
Continuous monitoring of your digital activities to detect and prevent threats.
Compliance-Ready Reports
Generate detailed GDPR, HIPAA, and SOC2 audit logs automatically.
Custom Policy Engine
Define redaction and access rules that match your internal compliance needs.
Enterprise Integration Layer
Plug-and-play API proxy compatible with major LLM providers.
Ready to Get Protected?
Join thousands of users who trust Valyn for their digital protection needs.